What is SAN storage and how it works?
A Storage Area Network is a high-speed sub network of shared storage devices. A SAN's architecture works in a way that makes all storage devices available to all servers on a LAN or WAN. As more storage devices are added to a SAN, they too will be accessible from any server in the larger network.
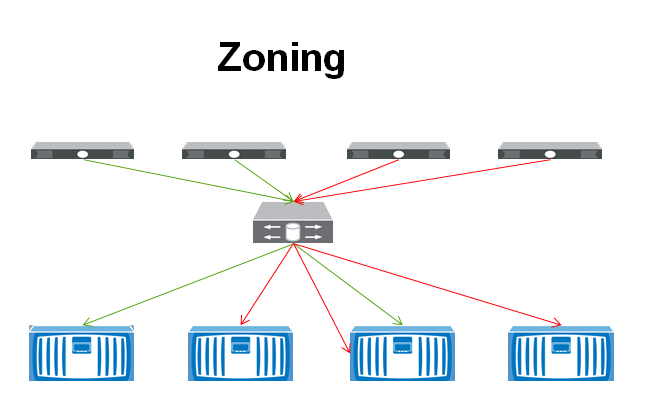
zoning
Zoning is done using a structure similar to that of a computer file system. A zone is the equivalent of a folder or directory. Zoning can be either hard or soft. In hard zoning, each device is assigned to a particular zone, and this assignment does not change. In soft zoning, device assignments can be changed by the network administrator to accommodate variations in the demands on different servers in the network.
The user of zoning is said to minimize the risk of data corruption, help secure data against hackers, slow the spread of viruses and worms, and minimize the time necessary for servers to reboot. However, zoning can complicate the scaling process if the number of users and servers in a SAN increases significantly in a short period of time.
Difference between SAN and NAS
:max_bytes(150000):strip_icc()/san-vs-nas-818005-v2-5c1042ba46e0fb0001bf6882.png)
Storage area networks (SANs) and network attached storage (NAS)
both provide networked storage solutions. A NAS is a single storage
device that operates on data files, while a SAN is a local network of
multiple devices.
The differences between NAS and SAN can be seen when comparing their
cabling and how they're connected to the system, as well as how other
devices communicate with them. However, the two are sometimes used
together to form what's known as a unified SAN.
SAN vs. NAS Technology
A NAS unit includes a dedicated hardware device that connects to a local area network, usually through an Ethernet connection.
This NAS server authenticates clients and manages file operations in
much the same manner as traditional file servers, through
well-established network protocols.
To reduce the costs that occur with traditional file servers, NAS devices generally run an embedded operating system on simplified hardware and lack peripherals like a monitor or keyboard and are instead managed through a browser tool.
A SAN commonly utilizes Fibre Channel interconnects and connects a set of storage devices that are able to share data with one another.
Important NAS and SAN Benefits
The administrator of a home or small business network can connect one NAS device to a local area network. The device itself is a network node, much like computers and other TCP/IP devices, all of which maintain their own IP address and can effectively communicate with other networked devices.
Given that the network attached storage device is attached to the network,
all the other devices on that same network have easy access to it
(given that proper permissions are set up). Because of their centralized
nature, NAS devices offer an easy way for multiple users to access the
same data, which is important in situations where users
are collaborating on projects or utilizing the same company standards.
Using a software program provided with the NAS hardware, a network
administrator can set up automatic or manual backups and file copies
between the NAS and all the other connected devices. Therefore, a NAS
device is also useful for the opposite reason: to offload local data to
the network storage device's much larger storage container.
This is useful not only to ensure that users do not lose data, since
the NAS can be backed up on a regular schedule regardless of the
end-user's ability to back up, but also to give other network devices a
place to keep large files, especially large files that are often shared
among other network users.
Without a NAS, users have to find another (often slower) means to
send data to other devices on the network, like over email or physically
with flash drives. The NAS holds many gigabytes or terabytes
of data, and administrators can add additional storage capacity to
their network by installing additional NAS devices, although each NAS
operates independently.
Administrators of large enterprise networks may require many
terabytes of centralized file storage or extremely high-speed file
transfer operations. While installing an army of many NAS devices is not
a practical option, administrators can instead install a SAN containing
a high-performance disk array to provide the needed scalability and
performance.
However, SANs are not always physical. You can also create virtual
SANs (VSANs) that are defined by a software program. Virtual SANs are
easier to manage and offer better scalability since they're hardware
independent and controlled entirely by easy-to-change software.
Lun Masking vs Zoning
Zoning and Lun Masking are often confused for each other, probably because both of them are used to restrict access to storage. They should both be used to secure the storage network and reduce unnecessary traffic.Zoning
If you want to specify only certain hosts from accessing a storage device then you would want to setup zoning. For instance, in the example below, you can see that the two servers on the right can access three of the four storage devices, whereas the two on the left can only access two of the SANs. This configuration is done on the Fibre Channel switch. iSCSI, NFS, and FCoE can also be segmented, but they would use typical TCPIP segmentation methods like setting up a VLAN.
There are two type of zoning techniques: Hard Zoning and Soft Zoning.
Soft zoning filters one device from seeing another device. However, if the ports are manually setup, the switch will not stop the devices from communicating. Hard zoning by comparison prevents one port from sending traffic to the other port and is more secure.
Zoning can also be setup based off the port or the World Wide Name (WWN). Port zoning grants access from one port on a switch to another port on a switch. This would require physical security to be setup around the Fibre Switch, because the zones could be changed around simply by moving the cables in the switch. This also makes it more of a struggle for management if switches need to be moved or re-cabled. WWN zoning is setup by allowing access between two WWNs which makes management a little easier, but also is susceptible to WWN spoofing which could allow access to the storage device.
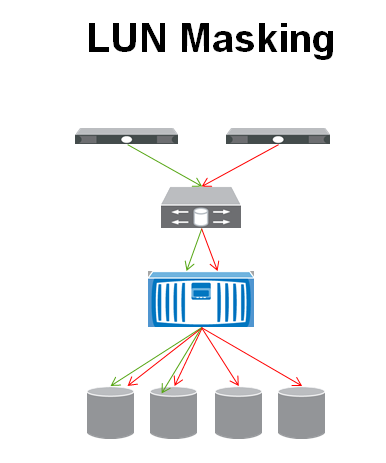
LUN Masking
Once the zoning is done, we can further lock down access to the storage by setting up LUN (Logical Unit Number) Masking on the storage device. The SAN would prevent certain devices from seeing a specific LUN that it is hosting. This may be used more to keep a misbehaving server from accessing a LUN that it doesn’t need access to more than it is a security concern.
In the Example below we have taken a small subset of servers that are accessing one storage device. The SAN is presenting four LUNs to the server on the right side (with the red arrows) but it is only presenting two LUNs to the server on the left (with the green arrows).