DevOps from Zero to Hero --> https://www.youtube.com/watch?v=Ou9j73aWgyE&list=PLdpzxOOAlwvIKMhk8WhzN1pYoJ1YU8Csa
Bala's Blog for Unix / Linux / AWS / Ansible
This blog contains details about Unix / Linux / AWS and Ansible. Kindly give me the feedback to get the right information on my blog.
Wednesday, September 24, 2025
Monday, February 5, 2024
Interview Questions for Linux/UNIX and Solaris
Linux Interview Questions
Important One - https://geekstuffweb.wordpress.com/2016/07/12/linux-interview-questions-and-answers-for-l2-and-l3-engineers/
https://testbook.com/interview/linux-troubleshooting-interview-questions
https://awstip.com/sre-devops-interview-questions-linux-troubleshooting-1b8ffe82c16
https://mindmajix.com/linux-interview-questions
https://linuxopsys.com/topics/linux-interview-questions-answers
https://tuxcare.com/blog/5-common-linux-server-problems-and-how-to-fix-them/
https://www.thegeekstuff.com/2011/12/linux-performance-monitoring-tools/
https://www.linuxscrew.com/category/linux/
Subscribed one - https://testbook.com/interview/linux-networking-interview-questions
https://www.nightwolf.in/nightwolf-cotribution/network/
Booting Process of Linux
https://www.freecodecamp.org/news/the-linux-booting-process-6-steps-described-in-detail/
Oracle - Exadata, PCA, ZFSSA, ODA, SuperCluster Definition and Function
1. Exadata,SuperCluster,ODA
https://licensingoracle.com/knowledge-center/exadata-supercluster/
2. Configuring an Oracle ZFS Storage ZS3-BA with an Oracle SuperCluster
3. Exadata Architecture
https://www.oracle.com/database/technologies/exadata/architecture/
4. Introduction to Oracle Exadata Database Machine and Oracle Exadata Storage Expansion Rack
Unix/Linux Command Reference
https://files.fosswire.com/2007/08/fwunixref.pdf
Linux Blog
https://learnlinuxconcepts.blogspot.com/2014/10/this-blog-is-to-help-those-students-and.html
Wednesday, April 26, 2023
Ansible
https://www.linuxsysadmins.com/ansible-playbook-to-create-users-and-groups/
http://minimum-viable-automation.com/ansible/use-ansible-create-user-accounts-setup-ssh-keys/
https://serversforhackers.com/c/create-user-in-ansible
https://docs.ansible.com/ansible/latest/collections/ansible/builtin/user_module.html
https://people.redhat.com/mskinner/rhug/q2.2017/Ansible-Hands-on-Introduction.pdf
Friday, December 18, 2020
Troubleshooting Solaris Interview Questions and Answers
https://www.unixarena.com/2013/06/solaris-scenario-based-interview.html/
https://mylearnjoy.wordpress.com/2015/11/18/solaris-l3-interview-questions-answers/
https://mindmajix.com/sun-solaris-administration-interview-questions
https://docs.oracle.com/cd/E19455-01/806-1075/806-1075.pdf
https://iqsanswers.com/sun-solaris-interview-questions-and-answers/
Friday, May 10, 2019
How to save LDOM configuration and restore from xml file
https://www.thegeekdiary.com/how-to-save-ldom-configuration-and-restore-from-xml-file/Saving LDOM configuration
# ldm list-constraints -x ldom_name > ldom_name.xml
To save constraints of all the domains :
# ldm list-constraints -x > all_ldoms.xmlRestoring LDOM configuration
There are 2 ways to restore a LDOM configuration. 1. Using ldm add-domain command and xml file 2. Using ldm init-system command and xml fileUsing ldm-add domain command
Build domain by using the xml file# ldm add-domain -i ldom01.xmlBind and start the LDOM# ldm bind ldom01 # ldm start ldom01Using ldm init-system command
1. Restore primary domain configuration Ensure that the current sp configuration is factory default. If not set it to factory default. Refer the post here. primary# ldm list-config | grep “factory-default” factory-default [current]primary# ldm init-system -r -i primary.xml -r -> reboot after configuration is complete -i -> specify xml file location2. Restore all domains configuration We can also restore all the domains configuration ata time using ldm init-system and xml configuration file.# ldm init-system -r -i all_ldoms.xmlAfter the system reboots, bind and restart all the domains.# ldm bind ldom01 # ldm start ldom01 # ldm bind ldom02 # ldm start ldom02
How to save LDOM configuration and restore from xml file
https://www.thegeekdiary.com/how-to-save-ldom-configuration-and-restore-from-xml-file/
Wednesday, April 3, 2019
SAN Related Questions and Answers..............
A Storage Area Network is a high-speed sub network of shared storage devices. A SAN's architecture works in a way that makes all storage devices available to all servers on a LAN or WAN. As more storage devices are added to a SAN, they too will be accessible from any server in the larger network.
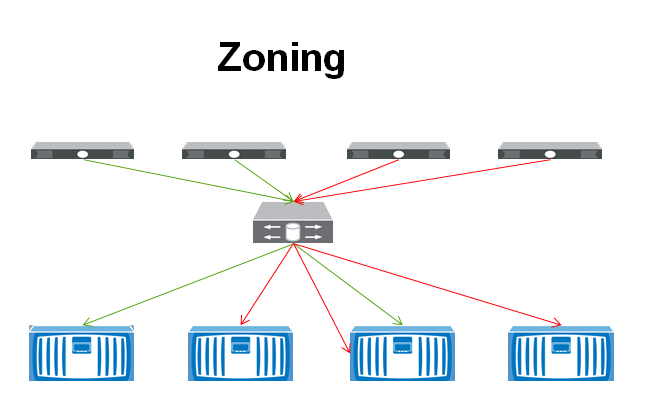
zoning
Zoning is done using a structure similar to that of a computer file system. A zone is the equivalent of a folder or directory. Zoning can be either hard or soft. In hard zoning, each device is assigned to a particular zone, and this assignment does not change. In soft zoning, device assignments can be changed by the network administrator to accommodate variations in the demands on different servers in the network.
The user of zoning is said to minimize the risk of data corruption, help secure data against hackers, slow the spread of viruses and worms, and minimize the time necessary for servers to reboot. However, zoning can complicate the scaling process if the number of users and servers in a SAN increases significantly in a short period of time.
Difference between SAN and NAS
:max_bytes(150000):strip_icc()/san-vs-nas-818005-v2-5c1042ba46e0fb0001bf6882.png)
SAN vs. NAS Technology
Important NAS and SAN Benefits
Lun Masking vs Zoning
Zoning and Lun Masking are often confused for each other, probably because both of them are used to restrict access to storage. They should both be used to secure the storage network and reduce unnecessary traffic.Zoning
If you want to specify only certain hosts from accessing a storage device then you would want to setup zoning. For instance, in the example below, you can see that the two servers on the right can access three of the four storage devices, whereas the two on the left can only access two of the SANs. This configuration is done on the Fibre Channel switch. iSCSI, NFS, and FCoE can also be segmented, but they would use typical TCPIP segmentation methods like setting up a VLAN.
There are two type of zoning techniques: Hard Zoning and Soft Zoning.
Soft zoning filters one device from seeing another device. However, if the ports are manually setup, the switch will not stop the devices from communicating. Hard zoning by comparison prevents one port from sending traffic to the other port and is more secure.
Zoning can also be setup based off the port or the World Wide Name (WWN). Port zoning grants access from one port on a switch to another port on a switch. This would require physical security to be setup around the Fibre Switch, because the zones could be changed around simply by moving the cables in the switch. This also makes it more of a struggle for management if switches need to be moved or re-cabled. WWN zoning is setup by allowing access between two WWNs which makes management a little easier, but also is susceptible to WWN spoofing which could allow access to the storage device.
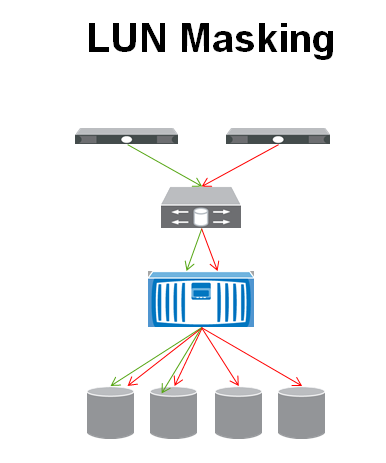
LUN Masking
Once the zoning is done, we can further lock down access to the storage by setting up LUN (Logical Unit Number) Masking on the storage device. The SAN would prevent certain devices from seeing a specific LUN that it is hosting. This may be used more to keep a misbehaving server from accessing a LUN that it doesn’t need access to more than it is a security concern.
In the Example below we have taken a small subset of servers that are accessing one storage device. The SAN is presenting four LUNs to the server on the right side (with the red arrows) but it is only presenting two LUNs to the server on the left (with the green arrows).
Tuesday, April 2, 2019
Friday, March 15, 2019
Thursday, January 3, 2019
Thursday, December 6, 2018
Friday, November 23, 2018
RHCSA EXAM Questions & Answers
**********************************************
* password for both virtual machine should be “Postroll”
*serverX.example.com provided with ip=172.25.X.11/255.255.255.0
*serverX.example.com are provided with gateway 172.25.254.254 & example.com dns domain with the IP: 172.25.254.254
* Set the Hostname
Before starting exam.
–> from server-vm ping base machine and server.
–> check hostname and IP address of server-vm and desktop-vm
(Note because partition sizes are seldom exactly what is specified when they are created, any thing within the range of 70MB to 120MB is acceptable)
(Note because partition sizes are seldom exactly what is specified when they are created,
any thing within the range of 130MB to 170MB is acceptable)
–> A user andrew who belongs to sysgrp as a secondary group
–> A user susan also belongs to sysgrp as a secondary group
–> A user sarah who does not have access to an interactive shell on system and who not a member of sysgrp
–> susan,sarah, andrew password = “Postroll”
–> Group owneship of /redhat/sysgrpis sysgrp
–> The directory should be readbale,writable, and accessable to members of sysgrp,
but not to any other user.
(It is understood that root has access to all files and directories on the system.
–> Files created in /redhat/sysgrp automatically have group ownership set to the sysgrp group
The following criteria must also be met:
–>The updated kernel is the default kerneal when the system rebooted.
–>The original kernel remains available and bootable on the system
Note the following:-
–> The LDAP search base DN is dc=example,dc=com
–> The LDAP certificate file is
http://classroom.example.com/pub/EXAMPLE-CA-CERT
–>ldapuserX should be able to log into your system, whereX is your ServerX ((hint:where X is your domain number),
but will not have a home directory, until you have completed the autofs requirement,below all LDAP users have password of “password”
Note the following:
–>classroom.example.com (172.25.254.254), NFS-exports /home/guests to your system, whereX is your server Number.
–>LDAP userX’s home directory is classroom.example.com:/home/guests/ldapuserX
–>LdapuserX’s home directory should be automounted locally beneath /home as /home/guests/ldapuserX
–>home directories must be writable by their users
–>while you are able to login as any of the users ldapuser1 through ldapuser20 the only home directory that is accessible from
your system is ldapuserX.
Example:- classroom.example.com would configure the automaster such that ldapuser100’s home directory /home/guests/ldapuserX gets mounted automatically upon login. The NFS share would be classroom.example.com:/home/guests/ldapuser100
configure the permission of /var/tmp/fstab so that
the file /var/tmp/fstab is owned by the root user, belongs to the group root
should not be executable by anyone.
The user andrew is able to read & write /var/tmp/fstab
The user susan can neighter write nor read /var/tmp/fstab
All other users (current or future) have the ability to read /var/tmp/fstab.
Make sure that the filesystem contents remain intact.
(Note: partitions are seldom exactly the size requested,so any thing within the range of 370MB to 430MB is acceptable)
create a new logical volume in the name of datacopy with the size of 50 extents and file system must vfat then
mount it under /datasource
DevOps from Zero to Hero --> https://www.youtube.com/watch?v=Ou9j73aWgyE&list=PLdpzxOOAlwvIKMhk8WhzN1pYoJ1YU8Csa
-
RHCSA EXAM Questions & Answers ********************************************** RHCSA-VM configuration: *you have been provided a v...
-
Solaris 10: Patching Solaris 10 on servers with non-global zones http://unixadminschool.com/blog/2011/10/solaris-10-patching-solaris-10-o...